More and more companies realize that server virtualization is the way to modern data security. In 2020, VMware is still the market leader, and many Veeam customers are using VMware vSphere as their preferred virtualization platform. But backing up virtual machines in vSphere is only part of the service availability. Backup is the backbone of recovery. So it’s important that backups are always available at the right speed.
This guide presents Veeam Backup & Replication best practices. It is not complete documentation or a detailed explanation of the features. The Best Practices Guide is for professionals looking for answers and suggestions on various topics. It may be a design idea, the best way to use a function, possible pitfalls, etc. D. As a rule, this information has been developed, collected, and updated by the Veeam Solutions Architects team working on site with Veeam users. They do not explain theory, but practice.
Note that the best practices are not the only available answer. In most cases it will work, but it may be completely wrong in other circumstances. Make sure you understand the recommended best practices, or ask someone to do so.
Table of Contents:
K.I.S.S. design

It becomes more difficult for the IT department to manage and ignore too complex projects, and it is easier for an intruder to use them and stay in the background. Projects that are easier and easier to ignore are usually safer. Use the K.I.S.S. (Keep it simple stupid) Principle for your creations. KISS is an acronym for “Keep it simple, stupid” as a design principle established by the US Navy in 1960. The principle of KISS states that most systems work best when they are simple and uncomplicated. Therefore, simplicity should be a key design objective and unnecessary complexity should be avoided. Simple design is easier to control and is generally safe.
Adding security to an existing infrastructure is much harder and more expensive than thinking about designing a new infrastructure or upgrading an existing one. In a virtual infrastructure, it makes sense to create a master image that has been enhanced from the beginning. Remove all known attack vectors and access only when Veeam components are added and certain (port) openings or additional software are required for correct operation. Thus, all versions are consistent and up-to-date, which makes them safe in the database.
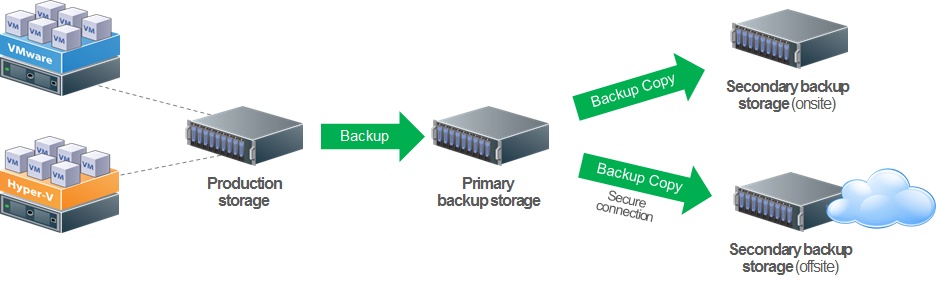
Make sure that the repository servers are physically protected.
Place the repository servers in a restricted area, because these servers contain a 100% copy of your production environment! The repository servers must be physically secure and have appropriate access control systems. This will restrict access. All those who have access are logged and controlled at certain defined levels.
Use a standalone Windows server

If you are protecting the entire environment, you do not want the Veeam repository to be associated with the same Microsoft Active Directory domain that you are protecting through a backup. Otherwise, you may have a chicken and egg problem with accounts trying to authenticate to a domain that is no longer available if everything is lost.
If the domain administrator account is compromised, we do not want that account to be able to override the password for the backup store account so that the hacker can access the backup files as well as the entire environment.
Protect physical or external cloud servers with Veeam Agent’s backup.
- You may have servers that Veeam cannot back up or replicate.
- Maybe physical servers or a virtual machine that is in a public cloud that you do not have access to a hypervisor (e.g. AWS),
Azure-blue). For these servers, you can back up the iland cloud repository using Veeam Agent. - Backups. This agent is installed in the guest operating system of the production server and does not require access at hypervisor level. Veeam Agent can be installed on Windows and Linux systems.
Note the bandwidth availability.

- The performance of Veeam Cloud Connect is highly dependent on the available bandwidth. For example,
- If you are trying to back up or replicate terabytes of data, but only 20 Mbps is available, you can
- Backing up should take a few days. The initial backup or replica may be important time, because all data has to be transmitted for the first time.
- When you can’t finish Timely progressive work can have a significant impact on your safety and confidentiality.
- It is also better to schedule external tasks outside working hours if possible. This allows you to allocate Veeam bandwidth instead of sharing it with your network end users.
Check your backups and replicas regularly.
The worst time to find out if your backups or replicas are damaged is when you need them. Check yours.
Backups and copies for replication to ensure that they are complete and acceptable when and how you do it
you need them. You can use Veeam Console to restore all VMs, VM files or guest OS files to your computer.
Surroundings. This process gives you confidence that your data will be available immediately if
There is a disaster.
- You can test the failover at any time and access your replicas in the iland cloud.
- This is useful not only to test the integrity of your replica data, but also to provide access to and
- The function works as it should. It may be necessary to update the existing network rules.
or that new critical servers have been added to production but not yet replicated.
Physical deployment
 In small to medium sized environments (up to 500 virtual machines), Veeam Backup and Replication Server, Backup Repository and Backup Proxy components are typically running on the same physical server. This is also known as deployment of a “model device”.
In small to medium sized environments (up to 500 virtual machines), Veeam Backup and Replication Server, Backup Repository and Backup Proxy components are typically running on the same physical server. This is also known as deployment of a “model device”.
In large environments (over 2500 virtual machines), Veeam’s backup and replication services work best on separate physical or virtual servers. When multiple jobs are running at the same time and consume large amounts of CPU and RAM, it may not be possible to scale up a virtual backup and replication server to meet system requirements.
One of the advantages of running Veeam Backup and Replication Server on a physical server is that it runs independently of the virtual platform. This may be an ideal situation where the virtualized platform is recovering from a disaster.
In an enterprise environment, you can install additional VBR to speed up the disaster recovery process. You can reuse existing availability components, such as a repository or proxy server, for Veeam Backup and Replication.
Backup Proxy
The Backup Proxy is a compact architectural component of Veeam that sits between the data source and the backup destination, processing backup jobs and providing backup traffic. Backup proxy server tasks include retrieving VM data from the production storage and compressing, deduplicating and sending this data to the backup repository. With more than one virtualized (or physical) backup proxy, you can easily scale your backup infrastructure to fit your system size.
- In a simple deployment scenario for small environments, Veeam Backup Proxy is automatically installed on the VBR as part of the Veeam Backup and Replication installation.
- In advanced deployments, the Proxy role is manually assigned to one or more Windows servers. This offloads the Veeam backup server, reducing backup time and improving performance.
